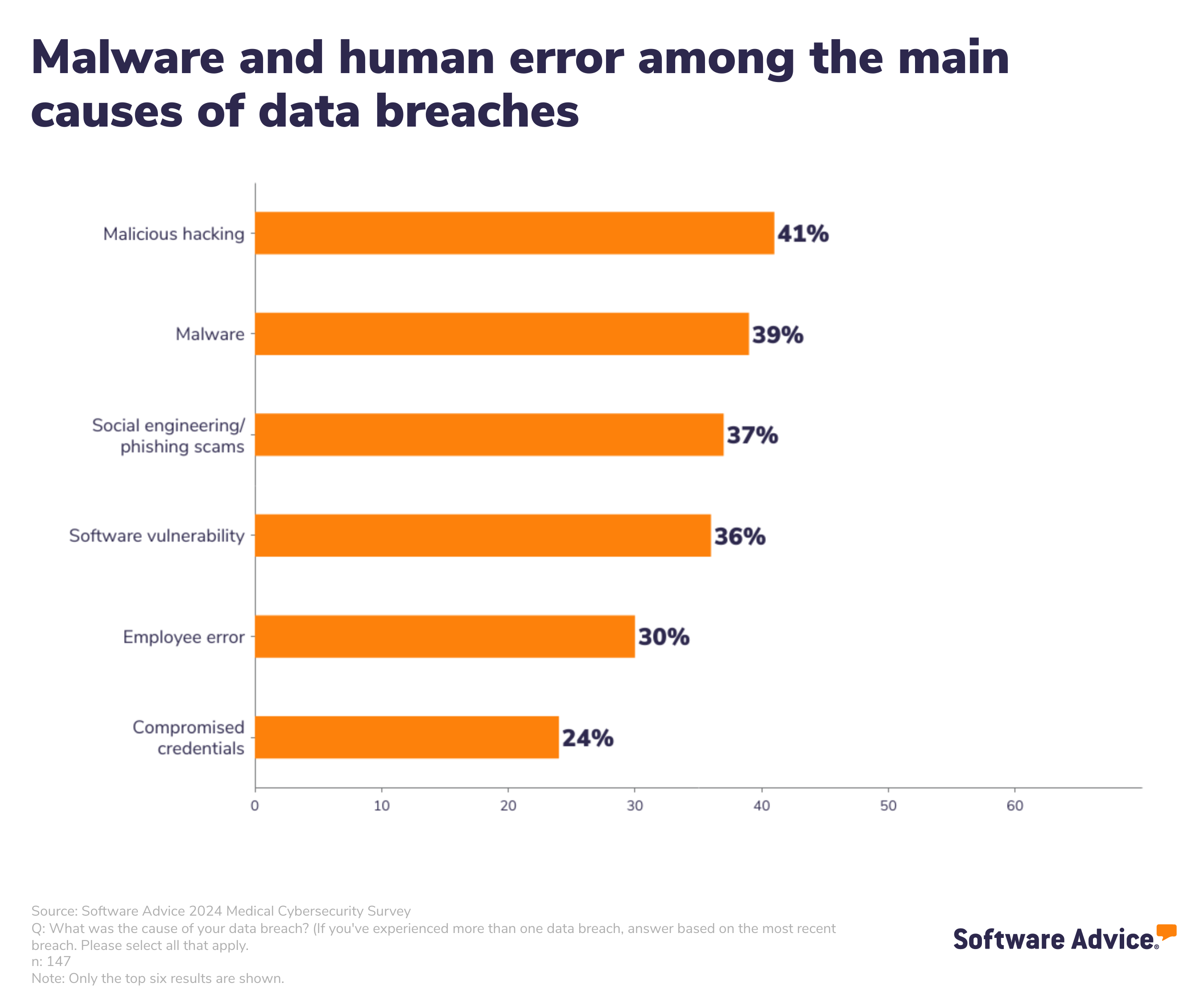
At least one-half of U.S. health care organizations have experienced a data breach, one-third in the last 3 years, according to Software Advice’s 2024 Healthcare Data Security Survey released in May 2024.
Of the health care organizations who experienced ransomware attacks, one-third did not recover patient data from the cyber-attackers, Software Advice learned.
Clearly, cyberattacks are impacting patient care. And the growth of home care, hospital-to-home, and greater self-care are also increasing risks for cybersecurity.
The growing adoption of digital technologies in healthcare, from the hospital to the doctor’s office to the home, are in the words of Greg Garcia, “increasing the attack surface.” Garcia is the executive director of the Healthcare and Public Health Sector Coordinating council Cybersecurity Working Group, and was recently quoted in Modern Healthcare discussing how home health care adds another opportunity and risk-exposure for cyber-attackers to exploit.

“The future of health will be characterized by lots of devices, lots of data, and lots of sharing—which will make radically interoperable data and open platforms key enablers of the innovative services and delivery models on the health care horizon,” Deloitte notes in its report on The future of cyber in the future of health.
With that context in mind, let’s start our third conversation with Richard Kaufmann, CISO of Amedisys, on the future(s) of cybersecurity in health care.
Jane: Richard, given the expanding proliferation of devices and care delivered across the health care ecosystem, we know that health care must be built on interoperability. But that means that one organization cannot secure everything or everyone, a recent report on health care cybersecurity from the World Economic Forum pointed out. WEF wrote that, “The strength of every single bond can determine the success or failure of our ecosystem.” What will ensure that health care organizations will play well in the cybersecurity sandbox with each other going forward?
Richard: Our healthcare system is a complex dance between Payers (Insurance Companies) and Providers (Doctors, Hospitals, and in the case of Amedisys – Home Health, Hospice, and Palliative Care.) I think it’s important to acknowledge how difficult it currently is for some patients to navigate their continuum of care.
As a simple example, think about something as benign as an annual check-up. That might look like a single event to the patient, but the data from that visit is sent to insurance companies, providers, and pharmacies as needed. One small event in a patient’s healthcare journey can generate data shared by dozens of entities. To your point above, each of the entities that interacts with that clinical data all have different security programs, different budgets, and different priorities for the protection of that data.

One of the fastest ways to ensure that organizations are taking security seriously is to empower the patients to ask questions. It should be a simple exercise for a patient to understand where their data is going and more importantly why. Patients have the power to set clear expectations for their privacy. The start of making real changes in security expectations must start with the consumer. [Comment from Jane: Cybersecurity is a key patient safety component, addressed in the public-private partnership on best practices for cybersecurity drafted by the Department of Health and Human Services and over 100 healthcare stakeholder organizations).
Jane: Will the growing adoption and pressure to “democratize” the use of AI in health care bring growing cybersecurity risks for the sector? How do we balance that democratization while risk-managing cyber-threats?
Richard: I would consider myself a very pro-AI security practitioner, which is very much the minority of security professionals these days. AI is going to be differentially disruptive to healthcare, but to get it there, we need to feed the insatiable appetite of the data models first. With every great leap in technology, risk tends to grow, but leveraging AI in a clinical setting is going to happen.
My experience has taught me that regardless of payor or provider, most successful healthcare organizations have a deep understanding of their patient populations and fluctuations within it. That insight exists today. We can take advantage of that insight because there are already some clear guidelines on how to de-identify Personal Health Information (PHI). De-Identified doesn’t mean de-valued. The frameworks that keep your information private in an analytical setting already exist. I think a responsible approach for training the Health AI models would follow a similar path.
I think demonstrating the value of faster, more accurate clinical decisions is one of the first steps in this AI revolution. The things that will keep the next generation of CISOs awake at night aren’t necessarily how the data is flowing into the data models: it’s going to be more of what are the intentions of the organizations behind the data models. If we’ve learned anything from the social media boom it is that just because technology enables us to do something doesn’t mean we should do so blindly.
Jane: Consider the convergence of “radically interoperable” data as Deloitte described with care delivered in a distributed fashion including to the citizen’s home, and the growing array of sensors and devices. In the U.S., will HIPAA be enough to assure the privacy of patients’ PHI in an AI-driven environment? What additional legal or regulatory guardrails would you imagine could be useful for confronting growing risks for cyberattacks in health care in the U.S.? Do we need a GDPR-like law to cover all 50 states?
Richard: I think cybersecurity is close to having the equivalent of what accounting went through two decades ago with Sarbanes-Oxley. You can see the start of it with the additional 8-K requirements for publicly-traded companies. HIPAA is also getting a little bit long in the tooth and that’s coming at an expense to innovation. I think the healthcare industry wants to move faster in some areas and at times that’s difficult because there is such a lag in regulations. It seems inevitable that regulators and practitioners are going to have to get together and set more defined expectations.
One thing important to keep in mind is that regulation isn’t a silver bullet. When done well it can provide structure and oversight, without being prescriptive. Here is why that’s important to a CISO: we deal, mostly, with criminals. Criminals don’t have to follow the rules. It really is a game of cat and mouse and while I would certainly welcome more structure from regulators, I also fully acknowledge that as soon as the structure is there, our adversaries will just move the needle again.
That’s where I see the largest opportunity right now: in the ecosystem of security. Organizations must have an outlet, generally through law enforcement, to stop the attacks from taking place. At times, law enforcement can struggle prioritizing cybercrime because it’s just so prevalent. I use this example all the time. If someone came to your house and knocked on the door at 2 AM, you would want the police to come and check on that. In cybersecurity our door is a firewall, and it is in a persistent state of being knocked on. Each day, our infrastructure is scanned, phishing and social engineering campaigns are spun up and wound down, and a small misconfiguration in an environment can have a disproportionate impact on operations. In addition to setting clearer expectations for organizations, I think there is a conversation to be had about how to better empower, fund, and partner with Law Enforcement Agencies. There must be more consequences for the individuals behind the attacks we hear in the news and often times that comes far too slowly if at all.
If we can align the regulatory, operations, and enforcement agencies with a more informed patient population regarding privacy, there isn’t a reason the U.S. couldn’t have something much better than just our own version of GDPR in place. It’s a massive effort to get all of those wheels moving in the same direction, but I do believe we are at a moment in time where more thoughtful regulation would be welcomed to most security leaders.

Jane: Human error is a major contributor to cyberattack risks in health care, the Software Advice survey learned. As we think about health care delivery in the future, and especially in your work of health care delivered in peoples’ homes and in the broader community, what will a resilient culture of cybersecurity look like? How do we continue to support empathy and the human touch in our staff while bolstering a “hard” response against potential cyber-attackers?
Being a clinician has always been a tough job. It’s a selfless act – providing care for someone else. Strip away everything else and healthcare is simply a population of people who feel a strong calling to make someone else’s life better. At Amedisys, we do that by either providing services that increase your wellness or increase your quality of life, but the core of our mission is compassion.
Mistakes are going to happen. The security organizations that excel are the ones who can limit the ramifications of mistakes the most. My advice to the CISOs out there wrestling with the question above, would be to focus on how your organization wants to work and design your security controls accordingly. Operations is like water – it’s always going to find the easiest and fastest path. For our security team at Amedisys, that looked like spending lots of cycles meeting with our clinicians and learning how they wanted to work. Then we strategically placed friction points where it made sense – mostly as just a check point in their daily routines.
Once you have that understanding, that empathy, for your caregivers, it gives you the autonomy to be more restrictive about everything else. One thing I can say from experience is that mistakes look completely different from malfeasance. There should be a fundamental understanding of how a business operates to distinguish between the two, but once you have it, that’s when a security leader can become a value add to a business. And that’s the job of a modern CISO – it isn’t just about securing; it’s about enabling the business to move as fast as they need to.
A postscript from Richard:
Jane – thank you for the opportunity to share some of my thoughts about security in the healthcare ecosystem. I would really like to acknowledge all the cyber professionals that show up every day, with very few days of thanks, much less praise from an outside perspective. I hope I can use this platform to let all of the security practitioners in the world know that your hard work is appreciated, if not always seen. The contribution you are making to our healthcare system is relevant and your work matters a great deal. To my current team and all the alumni of our security program at Amedisys – thanks for everything that you’ve done to help keep our patient’s privacy at the forefront of our program and for all the late nights and laughs along the way.





 Grateful to Gregg Malkary for inviting me to join his podcast
Grateful to Gregg Malkary for inviting me to join his podcast  This conversation with Lynn Hanessian, chief strategist at Edelman, rings truer in today's context than on the day we recorded it. We're
This conversation with Lynn Hanessian, chief strategist at Edelman, rings truer in today's context than on the day we recorded it. We're