 The growth of data, small and Big, in health care motivates the industry’s stakeholders to adopt technologies that help store, manage and analyze data to drive knowledge and, ultimately, individual and public health. Healthcare is embracing cloud technology, mobile platforms, social networks, e-commerce, robotics, and the Internet of Things (IoT), among a growing list of tech innovations.
The growth of data, small and Big, in health care motivates the industry’s stakeholders to adopt technologies that help store, manage and analyze data to drive knowledge and, ultimately, individual and public health. Healthcare is embracing cloud technology, mobile platforms, social networks, e-commerce, robotics, and the Internet of Things (IoT), among a growing list of tech innovations.
Each of these innovations, which enable productivity and economic growth, also present cybersecurity risks. The value of these risks is estimated to be as much as $3 trillion to the global economy, according to McKinsey’s calculations in the report Risk and Responsibility in a Hyperconnected World, developed in conjunction with the World Economic Forum‘s annual meeting in Davos, Switzerland, in January 2014.
I’m re-visiting this report now that my own paper Here’s Looking at You: How Personal Health Information is Tracked and Used was published last week by the California HealthCare Foundation. McKinsey’s work dovetails into my own research into consumer-generated data – “small data” – and the growing world of Big Data, cybersecurity and individuals’ health information privacy in the “hyperconnected health” world where HIPAA lacks teeth and authority.
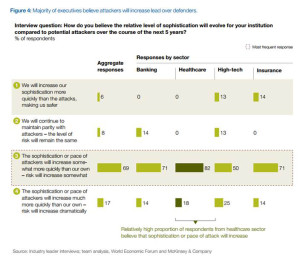 The top-line: vigilantly protecting data in the healthcare enterprise ultimately protects people and, specifically, health citizens. And health enterprises, more than banking, high-tech and insurance, believe that the sophistication and pace of attackers is increasing more quickly than healthcare’s own ability to deal, as the second graphic attests.
The top-line: vigilantly protecting data in the healthcare enterprise ultimately protects people and, specifically, health citizens. And health enterprises, more than banking, high-tech and insurance, believe that the sophistication and pace of attackers is increasing more quickly than healthcare’s own ability to deal, as the second graphic attests.
While the report covers the world macroeconomic impact of cybersecurity, McKinsey identifies four key vertical markets where this issue can hit hard: banking, high-tech, insurance and healthcare. The 3 realities on cyber-resilience across industry sectors is that (1) it’s not an isolated issue, (2) it’s not one single issue (instead, a set of issues including but not limited to retail fraud, organized crime, personal privacy invasions, diplomacy, warfare, intellectual property, terrorism and activism among them), and (3) it’s a socio-economic issue, usually addressed as technical-political, not so much economic.
Still, McKinsey points out in the report’s introduction that we shouldn’t adopt a doomsday or “cybergeddon” view on this topic. We can prepare, rehearse, replay, refine, and continue to do so ongoing, to best deal with cybersecurity. While it’s easy to slip into a glass-half-empty mindset, Basel Kayyali of McKinsey spent time with me to talk about the implications of this report overall and for healthcare in particular.
The good news first, Kayyali notes, is “the recognition in industry that there is a problem around cybersecurity. A narrative in a lot of clients is they know stakes are very high. A breach has detrimental impact on the enterprise as a whole and on the consumer and patient’s trust with that enterprise.”
With wide recognition about cybersecurity challenges among health enterprises, they are allocating big money to the avoid data breaches. However, Kayyali says there’s also recognition that the health industry isn’t doing this in an efficient way. “There’s a surprising amount of alignment around how to prepare, how to get a return on the money being spent,” Kayyali finds – where “return on investment” here means better protection for the patient and consumer.
 McKinsey’s report identifies four business-process levers that can make a difference in health enterprises’ protecting patient and consumer data.
McKinsey’s report identifies four business-process levers that can make a difference in health enterprises’ protecting patient and consumer data.
- Prioritize information assets and risks. In healthcare, it is often the IT department controlling the cyber-investments, oftentimes working isolation separated from the business users. The most valuable information assets are often not those getting the investments, such as “highly synthesized data” not attributable back to an individual patient and provider, or data that CMS makes publicly available.
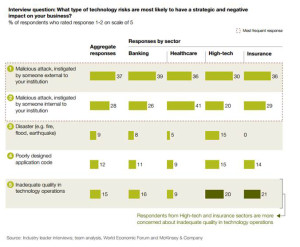
- Enlist front-line personnel. In healthcare, a great proportion of breaches are caused by internal actors, not external hackers, exhibited in the third chart. Thus, education and policy-setting in healthcare enterprises is a crucial linchpin for managing cybersecurity risks. Kayyali describes this as “allowing whistleblowing to get to the right people quickly and not to get ignored in the enterprise.” Looking at the high-profile data breaches in retail over the past two years, it’s been well-documented that data at terminals was being exposed and extracted but largely ignored by people in the “data food chain.” “How do you get that front line to understand the value of the asset and create channels that allow it to escalate?” Kayyali challenges the industry.
- Integrate cyber-resilience through the enterprise. Organizations should practice for cybersecurity as they do for fire drills. What happens as information gets breached? What should people do to respond? What’s the escalation path? How do we mobilize to stunt risk and damage to patients and consumers? Many organizations do not have clear processes, and practice and rehearsal in simulations can help the organization become cyber-resilient in real-time.
- Integrate incident response across all business functions. Doing so can bolster cyber-security processes as second-nature to a healthcare organization.
There are three additional levers that are more technology-focused: first, design the technology stack or solution with cybersecurity built-in and tightly integrated into the infrastructure to minimize holes that hackers can exploit. Second, create differentiated protection for the most important assets prioritized, and put sufficient resources to the highest-priority risks. And third, operate “active defense,” and conquer attacks early.
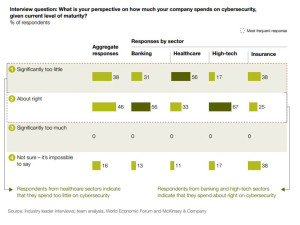 Health Populi’s Hot Points: Healthcare is one of the most valuable industry sectors in terms of cybersecurity risks noted in this report. There are mega-dollars involved – and, to be sure, peoples’ lives, livelihoods, and reputations at-stake. Healthcare leaders say they’re spending significantly too little money on cybersecurity, shown in the fourth chart.
Health Populi’s Hot Points: Healthcare is one of the most valuable industry sectors in terms of cybersecurity risks noted in this report. There are mega-dollars involved – and, to be sure, peoples’ lives, livelihoods, and reputations at-stake. Healthcare leaders say they’re spending significantly too little money on cybersecurity, shown in the fourth chart.
Kayyali noted an executive telling him that, “when someone steals your social security number, it’s a real pain but you can get a new one and clean up your credit scores. But if somebody steals your clinical data and finds out you have AIDS, you can’t claw that privacy back.” The stakes in dealing with clinical and health care data are very high.
Trust is the first ingredient enabling health engagement, we learned in the 2008 Edelman Health Engagement Barometer. Without that, people won’t share their personal data (health and lifestyle alike), and won’t fully participate in the health care system, which includes conducting research studies with robust patient profiles to solve big health issues.
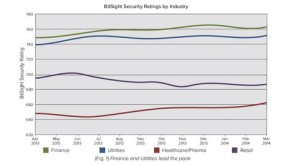 BitSight Technologies published survey research in May 2014 asking the question, “Will Healthcare Be The Next Retail?” BitSight’s security ratings for healthcare have been consistently lower than for finance, utilities and retail, as the last chart illustrates. The company observed that the healthcare sector shares many characteristics with the retail sector including a high volume of security incidents and slow response times.
BitSight Technologies published survey research in May 2014 asking the question, “Will Healthcare Be The Next Retail?” BitSight’s security ratings for healthcare have been consistently lower than for finance, utilities and retail, as the last chart illustrates. The company observed that the healthcare sector shares many characteristics with the retail sector including a high volume of security incidents and slow response times.
It’s regrettable that retail stores put shoppers’ personal data at-risk by lacking vigilance and cyber-resilience in their organizations. It’s mission-critical for health enterprises to grow cyber-resilient muscles to bolster patients’ and health citizens’ confidence in their providers, health plans, and industry suppliers (including but not limited to pharma, life sciences, and medical device companies). It will truly take health’s ecosystem-village to become cyber-resilient in health care. This is especially timely (and ironic) as healthcare in the U.S. continues to morph toward consumer-facing, retail mode.




 I am so grateful to Tom Lawry for asking me to pen the foreword for his book, Health Care Nation,
I am so grateful to Tom Lawry for asking me to pen the foreword for his book, Health Care Nation,  I love sharing perspectives on what's shaping the future of health care, and appreciate the opportunity to be collaborating once again with Duke Corporate Education and a global client on 6th May. We'll be addressing some key pillars to consider in scenario planning such as growing consumerism in health care, technology (from AI to telehealth), climate change, and trust -- the key enabler for health engagement or dis-engagement and mis-information. I'm grateful to be affiliated with the corporate education provider
I love sharing perspectives on what's shaping the future of health care, and appreciate the opportunity to be collaborating once again with Duke Corporate Education and a global client on 6th May. We'll be addressing some key pillars to consider in scenario planning such as growing consumerism in health care, technology (from AI to telehealth), climate change, and trust -- the key enabler for health engagement or dis-engagement and mis-information. I'm grateful to be affiliated with the corporate education provider  Thank you FeedSpot for
Thank you FeedSpot for